[Cryptography] RSA3
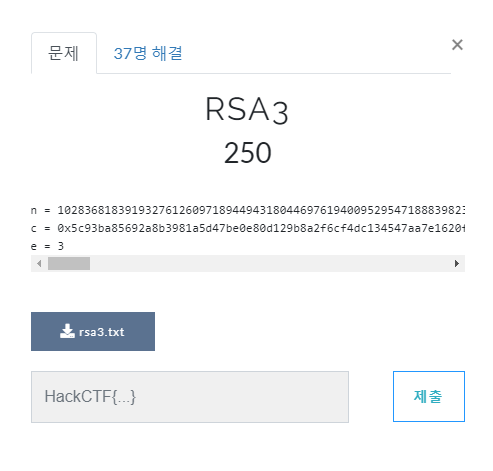
n = 10283681839193276126097189449431804469761940095295471888398234447479454966284763902940257262270896218602885591849219329295416054197234326881779747263501982465102957508563705432633950651360492963151374387619070656704554971992649022858286686244477458518219811343940208016922937570643216329114427596008380607613093481777894261584227765149699743645734317383348201997748556656749211035951710759363655486663011079526697122026161182876988679088458171192764980121987583057238040415225285169219391637708267493561674900564748140379192079752942242600521017002960185256025253900075152690586476143729320416895984549165574371936823
c = 0x5c93ba85692a8b3981a5d47be0e80d129b8a2f6cf4dc134547aa7e1620f6691513b1dc1d69e085c39e261c2b49026436bb243dba70a86f7fcd1a3a7e6b0f0ecfac015becad0a76e9cf208d5d31e2b4865
e = 3
해당 문제는 낮은 지수 공격으로 e 값은 작고 n 값은 매우 큰 경우이다.
[Exploit]
from gmpy2 import *
c = 0x5c93ba85692a8b3981a5d47be0e80d129b8a2f6cf4dc134547aa7e1620f6691513b1dc1d69e085c39e261c2b49026436bb243dba70a86f7fcd1a3a7e6b0f0ecfac015becad0a76e9cf208d5d31e2b4865
with local_context() as ctx:
ctx.precision = 3000
m = cbrt(c)
#m = iroot(c, 3)[0]
print ('%x' % int(m)).decode("hex")'CTF > HackCTF' 카테고리의 다른 글
| [Pwnable] Basic_FSB (0) | 2020.02.03 |
|---|---|
| [Cryptography] XOR (0) | 2020.02.03 |
| [Cryptography] RSA2 (0) | 2020.01.11 |
| [Cryptography] DNA (0) | 2020.01.11 |
| [Cryptography] Classic Cipher -4 (0) | 2020.01.11 |